Introducing Morpheus
A complete External Attack Surface Management (EASM) platform providing value across the security organisation.
Monitor your external perimeter to discover known and unknown assets, run vulnerability assessments at scale against new threats and proactively avoid common security misconfigurations.
Who Benefits?
Morpheus centralizes attack surface monitoring, threat visibility, streamlines vulnerability assessment and enhances decision-making for analysts, engineers and CISOs who can leverage the platform’s intuitive structure to support their EASM processes.

Leverage actionable insights on assets, technologies, vulnerabilities and emerging threats.
Analysts

Integrate seamlessly an enterprise-ready automated platform that continuously monitors your external perimeter.
Engineers

Free up time for your valuable team members, enable collaboration and get executive level reporting.
CISO
features

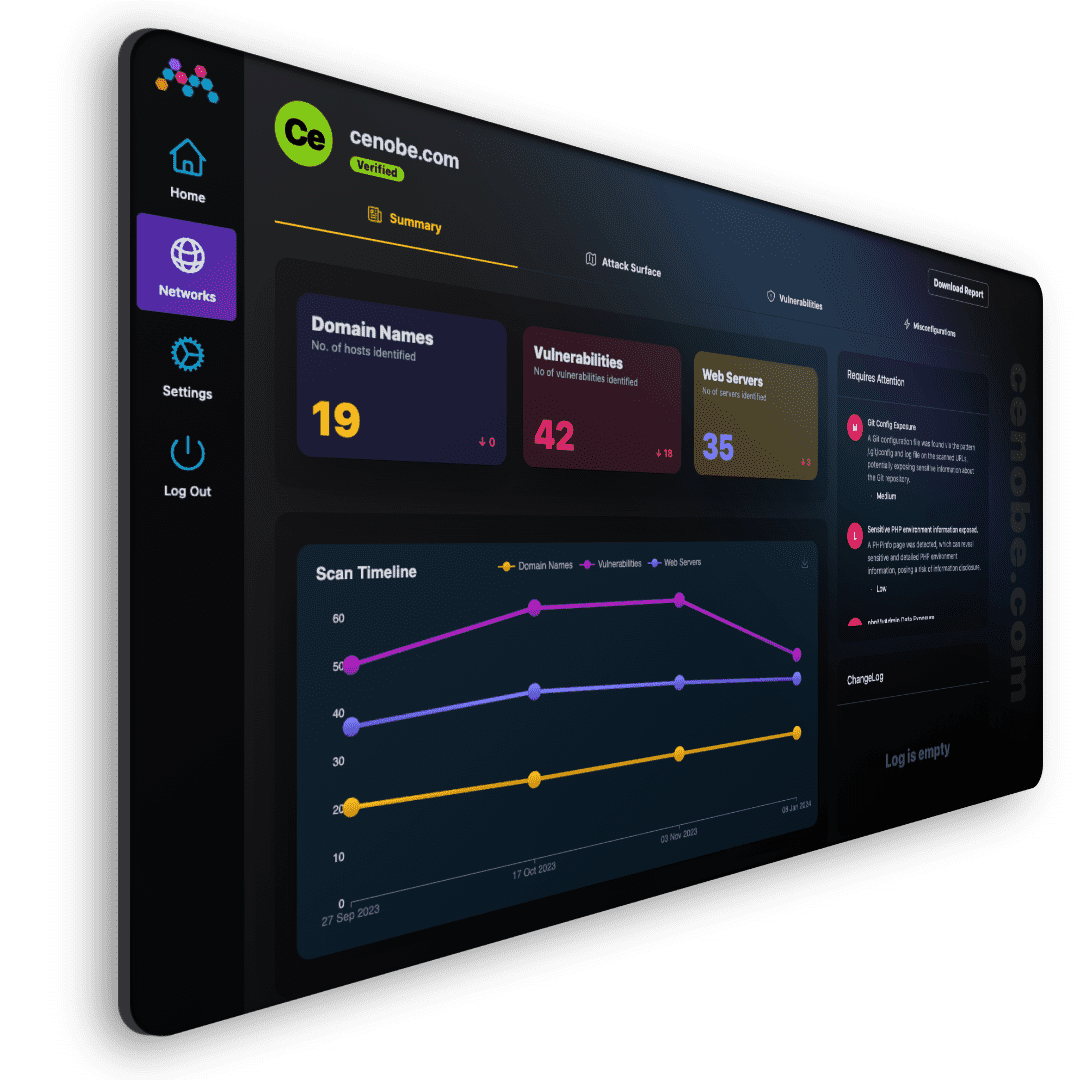
External Attack Surface Management
Morpheus’ cutting-edge technology conducts continuous discovery of all assets. This provides you with a holistic view of your attack surface, enabling a proactive mindset when enhancing your security posture.
Automated Vulnerability Assessment
Equipped with continuously updated and state-of-the-art vulnerability scanners, developed internally by our penetration testers, Morpheus continuously scans your assets for vulnerabilities, misconfigurations and all the latest CVEs as soon as they become public. Continuous automated assessment allows your organisation to drastically decrease the required time from detection to remediation.
Threat Intelligence & Security Metrics
Morpheus empowers organisations to assess their cybersecurity posture efficiently with its advanced security metrics functionality. By leveraging comprehensive data analysis and visualisation techniques, our platform enables you to quantitatively measure various security aspects.

Reporting
Morpheus' intuitive interface generates comprehensive reports transforming complex findings into concise summaries. The platform offers the flexibility to create both technical and executive reports effortlessly. This way of reporting allows you to efficiently communicate critical security information for tactical or strategic decisions.

Enterprise Ready
We know that there are no two organisations working in the same when it comes to cybersecurity and that is why our enterprise features allows us to adjust the platform according to your processes and EASM strategy.
When you compare Morpheus against other EASM platforms
We acknowledge the hard work other companies are putting to provide cutting-edge platforms to enable Attack Surface Management or enhance other areas of cybersecurity operations. However, we know where you will find value when choosing Morpheus.
- Levereging new technologies
Our penetration testers and security engineers have been using similar platforms and their own tools for several years before starting developing Morpheus. This allowed them to have a deep understanding of the requirements and features the platform should have. The platform has no legacy technologies and the architecture allows us to have a robust roadmap to scale scanning capabilities and to include new features according to our client’s requirements.
- Customisation to enable consolidation
A cybersecurity platform consists of several modules and features and must come with certain enterprise features to even make it possible for you as an evaluator to start the conversation. An SSO, an Integration or a configuration on how an EASM platform might need to get adjusted to certain uniqueness of your external facing assets should not be a reason for adding extra zeros to the invoice. Our pricing is based on the amount of subdomains you are monitoring and not on whether you need 2FA or API access.
- Cenobe - An offensive security team
Having an R&D department and an offensive security team working continuously with large enterprises around the world for penetration testing, red teaming or threat intelligence, allows us to have a much more holistic view of the threat landscape and the challenges the practitioners are facing today.